Weekly Threat Briefing: Save the Children Hit by $1M BEC Scam
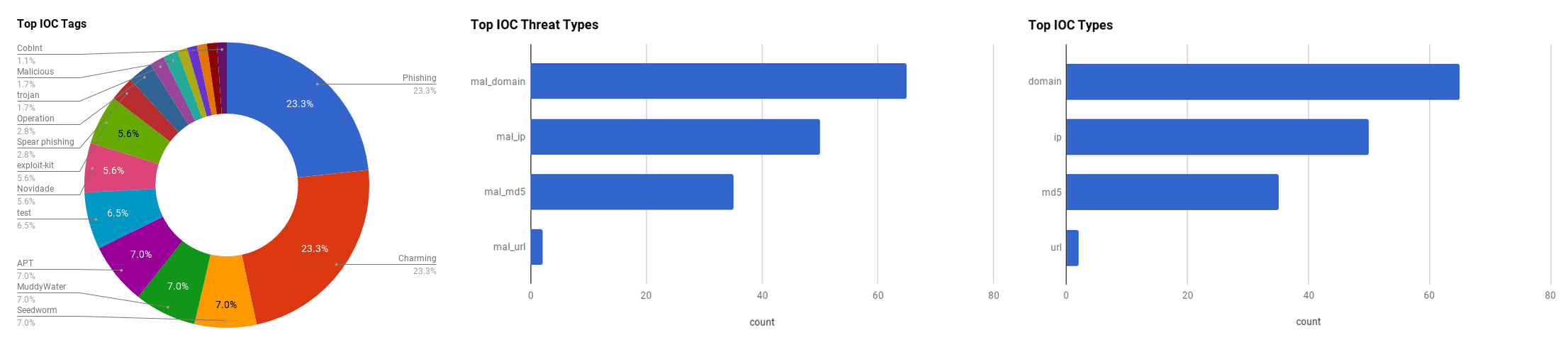

The intelligence in this weekís iteration discuss the following threats: Android trojan, BEC, Charming Kitten, Coblat Group, Exploit kit, Malware, Novidade, Phishing, Seedworm, SplitSpectre, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Save the Children Hit by $1m BEC Scam (December 17, 2018)
The American post for the UK-based charity, "Save the Children Federation," released that they had been a victim to a Business Email Compromise (BEC) following filing their taxes with the Internal Revenue Service (IRS). The unknown threat actor managed to somehow access an employee's email account and then sent the organisation fake invoices for solar panels for a Pakistani health centre, along with other documents. The money was transferred to a Japanese bank account prior to the discovery of the scam, and the organisation was able to recover all but $112,000 of the money sent.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194)
Critical SQLite Flaw Leaves Millions of Apps Vulnerable to Hackers (December 14, 2018)
A critical vulnerability in the popular database software, "SQLite," has been discovered by researchers from Tencent's Blade security team. This vulnerability has been called "Magellan" and allows for threat actors to remotely execute arbitrary and/or malicious code on machines, leak program memory, or even crash applications. Researchers were able to develop a successful Proof-of-Concept (PoC) exploit with the vulnerability, though they will not release the technical details or PoC publicly until patches for all applications are released. This vulnerability affects a large variety of users and applications such as Adobe, Apple, Android, Chrome, Dropbox, FireFox, Internet-of-Things (IoT) devices, Microsoft, and many others that utilise SQLite for their disk-based relational database management. SQLite has released an updated version of their software to address this issue.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064)
Operation SharpShooter Attacks Nuclear, Defense, Energy, and Financial Companies (December 13, 2018)
Over 87 organisations across 24 countries have been targeted in a recent spear phishing campaign, dubbed "Operation SharpShooter," according to McAfee researchers. The campaign targets institutions in the defence, energy, financial, and telecommunications sectors narrowing on English-speaking organisations in Australia, Europe, India, Japan, the Middle East, South America, and the US. The observed phishing emails were themed around recruitment, containing a seemingly legitimate job description and Word document attachment from a man named "Richard." The document requests macros to be enabled, and if allowed, an embedded shellcode injects a downloader for a backdoor called "Rising Sun." This allows for the threat actor to gain reconnaissance capabilities on the machine and obtain information such as documents, network configurations, system settings, and usernames that then sends the information to the designated Command and Control (C2) server. Interestingly, the malware can delete its history and clear memory to make detection difficult.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
The Return of The Charming Kitten (December 13, 2018)
Researchers from Certfa have observed the Advanced Persistent Threat (APT) group "Charming Kitten" is active again and conducting spear phishing attacks against targets who are from countries associated with the most recent sanctions placed upon Iran. In October 2018, the APT group was reported to have been observed attacking US financial institution infrastructure, potentially as a reaction to the sanctions placed against Iran. In November 2018, the domain "accounts[-]support[.]services," believed to be associated to Charming Kitten, was found to be used to target human and civil rights activists, political figures as well as Iranian and Western journalists in phishing attacks. The APT group initiates contact via email or social media, or via compromised accounts of known public figures, and notifies their targets with fake alerts of unauthorised users attempting to access their accounts. This alert then prompts the user to enter their username and password credentials to "secure" their account on a fake Google login page, which then gives the APT group access to those credentials.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Access Token Manipulation (T1134)
New Bomb Threat Email Scam Campaign Demanding $20K in Bitcoin (December 13, 2018)
A new phishing email extortion campaign has been observed targeting a variety of people in the US. The email contained a bomb threat that purported a device was in the building and required $20,000 USD in Bitcoin to prevent remote detonation of the bomb. A Twitter user under the name of "Defender" reported that there were over 15,000 incidents of these spam emails which have apparently originated from Russia. The New York Police Department began investigating the bomb threats and found the threats to be uncredible thus far.
Click here for Anomali recommendation
Cryptocurrency Miner Spreads via Old Vulnerabilities on Elasticsearch (December 12, 2018)
A cryptomining attack was observed to be exploiting known vulnerabilities for search engine "Elasticsearch" that are registered as "CVE-2015-1427" and "CVE-2014-3120," according to researchers at Trend Micro. CVE-2015-1427 is a vulnerability in Elasticsearch's "Groovy" scripting engine that can allow for remote arbitrary commands to be executed. CVE-2014-3120 is a vulnerability in Elasticsearch's default configuration that can allow for remote execution of arbitrary MVEL expressions and Java code. The attacks attempt to install cryptominers onto the infected machine through running a command that attempts to distribute a bash script to evoke the shell to run and download the mining malware. The threat actor will then run arbitrary commands to obtain privilege escalation and attempt to pivot to other systems connected to the network. The actual mining file is called "devtools" in the script in an attempt to obfuscate it on the machine, and once installed, it will search for other miners in the system and kill those to prevent them from restarting so it has sole control. It runs every ten minutes to mine for as much cryptocurrency as possible from the system. It is unclear whether the malware is mining for a specific type of cryptocurrency.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064) | [MITRE ATT&CK] .bash_profile and .bashrc (T1156)
Android Trojan Steals Money from PayPal Accounts Even with 2FA on (December 11, 2018)
Researchers from ESET detected a new trojan that has been infecting Android devices to target the official PayPal application. The trojan is distributed via malware found in a fake battery optimisation application found in third-party stores and exploits the Android Accessibility services. The fake battery-optimiser tool offers zero functionality and hides its icon whilst it attempts to gain accessibility service functions on the device. It will request the "enabling of statistics" and then alert the user to launch the official PayPal application if it is already loaded onto the device. Once the user logs into the application, the malicious accessibility service will intervene and mimic the user's clicks to send the threat actor money (1000 euros though currency depends on the user's location) to their PayPal account. The malware also uses phishing displays over legitimate applications such as Gmail, Google Play, Skype, Viber, and WhatsApp, with a credit card details page. This then gives the card credentials to the threat actors.
Click here for Anomali recommendation
Bug Affected 52.5 Million Users in Connection with a Google+ API (December 11, 2018)
Following a software update in the Google+ API in November 2018, the software had a new flaw that enabled applications to view 52.5 million Google+ users' profile information regardless of whether it was set to "public" or "private." Information that was accessible by unauthorised users and applications include age, email address, name, and occupation, amongst others. Google fixed the issue within a week of discovering the breach, and is investigating whether or not users' financial data, passwords, and other sensitive material were exposed due to this flaw. Google is in the process of notifying affected customers, and has announced that they will be accelerating the retirement of Google+ four months earlier than initially stated and are now pushing the retirement date to April 2019.
Click here for Anomali recommendation
Cobalt Group Pushes Revamped ThreadKit Malware (December 11, 2018)
The Advanced Persistent Threat (APT) group, "Cobalt Group," has been observed by researchers from Fidelis to have begun using a new version of the "ThreadKit" exploit kit. The group is distributing ThreadKit via a phishing campaign of theirs delivers a RTF Microsoft Office attachment that contains the exploit kit with the "CobInt" downloader delivered as the final payload. ThreadKit is observed to have slightly advanced its obfuscation techniques where it now places an "M" from the executable file into its own object, and has a XOR routine that is used to decode the initial CobInt payload. Despite the recent arrests of the suspected leaders of Cobalt Group, they are still highly active.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
Hackers Steal Over 40k Logins for Gov Services in 30 Countries (December 11, 2018)
More than 40,000 users across the globe fell victim to a phishing attack that compromised various online government services accounts. Unknown threat actors sent phishing emails that distributed spyware such as Pony Formgrabber, AZORult, and Qbot (Qakbot) that logged username and password credentials for civilians, government employees, and military officials in. The targeted individuals resided in or were affiliated to the following: Bulgaria, Croatia, France, Hungary, the Israel Defence Forces, the Ministry of Finance of Georgia, the Ministry of Foreign Affairs of Romania, the Italian Ministry of Defence and Foreign Affairs, the Norwegian Directorate of Immigration, Poland, Romania, and Switzerland. The malicious attachment pretended to be a legitimate file and, if opened, would target credentials located in configuration files, databases, and secret storages that would then be sent to the threat actor's Command and Control (C2) server.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
A Bug Left Your Microsoft Account Wide Open to Complete Takeover (December 11, 2018)
Sahad Nk, a bug bounty hunter, found several Microsoft vulnerabilities that left users' accounts vulnerable to unauthorised actors accessing Microsoft users' accounts. Nk noticed that "http://success.office[.]com" was not configured properly, thus allowing him to take control over the subdomain and subsequently any information that was sent to it. This subdomain also received authenticated login tokens for Microsoft Office, Outlook, Store, and Sway. This meant that NK could obtain the login token and then use that token to access an account without needing a username or password.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Access Token Manipulation (T1134)
New Exploit Kit "Novidade" Found Targeting Home and SOHO Routers (December 11, 2018)
A new exploit kit, dubbed "Novidade," that targets home and small office routers has been discovered by researchers at Trend Micro. The exploit kit is delivered via malvertising, compromised websites, and instant messengers. If a target clicks upon a link that leads to Novidade, several HTTP requests will be generated to a predefined list of IP addresses that are used by routers. If a connection is established successfully, the exploit payload will download and attack the IP with various exploits. It then attempts to brute force the connected routers. If a router is successfully compromised, the original Domain Name System (DNS) is altered to the threat actor's DNS server. This redirects all devices connected to the infected router to the threat actor-controlled sites. The compromised router will redirect any traffic that attempts to access targeted bank domains to a fake banking website.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194) | [MITRE ATT&CK] Brute Force (T1110)
Seedworm: Group Compromises Government Agencies, Oil & Gas, NGOs, Telecoms, and IT Firms (December 10, 2018)
Researchers from Symantec have found that the Advanced Persistent Threat (APT) group "Seedworm" (also known as "MuddyWater") has been actively targeting various organisations in the Middle East and Asia with a new version of their custom backdoor "Powermud." The APT group is believed to be an Iranian cyber espionage group that works to obtain information through backdoors and custom password stealing tools, amongst others. The Powermud backdoor was observed to be on machines in Afghanistan, Armenia, Egypt, Jordan, Pakistan, Russia, Saudi Arabia, and Turkey, amongst several others. The highest infection rates were found to be in Pakistan and Turkey. Once in a network, the APT group will run a password-stealing tool to obtain passwords saved in users' web browsers and email. They then utilise open-source tools such as "LaZagne" and "Crackmapexec" to obtain Windows authorisation credentials to achieve persistence and privilege escalation in the infected network.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation for Privilege Escalation (T1068)
SplitSpectre ñ New Spectre-like Vulnerability Ready to Hit CPUs (December 10, 2018)
A new vulnerability has been discovered by researchers from Northeastern University and IBM that could allow for speculative execution attacks, dubbed "SplitSpectre." This vulnerability is a Spectre v1 variant, and allows for a threat actor to exploit the speculative execution function of microprocessors without having to inject their own malicious code. According to the research paper produced by the researchers who identified this vulnerability, the SplitSpectre vulnerability "splits the Spectre v1 gadget into two parts: one consisting of the conditional branch and the array access (phase 3), and the other one consisting of the second array access that constitutes the sending part of the side channel (phase 4). This has the advantage that the second part, phase 4, can now be placed into the attacker-controlled code. It is more likely that an attacker finds such gadgets, thereby alleviating one of the main difficulties of performing a v1 attack. Furthermore, the attacker can choose to employ amplification of a v1 attack by reading multiple indices of the second array to deal with imprecise time sources."
Click here for Anomali recommendation
Satan Ransomware Variant Exploits 10 Server-Side Flaws (December 10, 2018)
Researchers from NSFocus discovered a new variant of the "Satan" ransomware, dubbed "Lucky," that has been observed to exploit ten different vulnerabilities in Windows and Linux server platforms. The Lucky ransomware is able to propagate within a system without human interaction, and appears to be targeted towards financial services. The vulnerabilities exploited to gain access and propagate include: "JBoss default configuration vulnerability (CVE-2010-0738), a Tomcat arbitrary file upload vulnerability (CVE-2017-12615), a WebLogic arbitrary file upload vulnerability (CVE-2018-2894), a WebLogic WLS component vulnerability (CVE-2017-10271), a Windows SMB remote code execution vulnerability (MS17-010), a Spring Data Commons remote code execution vulnerability (CVE-2018-1273), an Apache Struts 2 remote code execution vulnerability (S2-045), an Apache Struts 2 remote code execution vulnerability (S2-057), and a Tomcat Web admin console backstage weak password brute-force flaw." Many of the vulnerabilities were disclosed within the past few months, which means there are likely many targets who are still susceptible to exploitation.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Notepad++ Attack, RAT Uses Hugging Face, Microsoft Office Flaw and more



