STIX-TAXII
What Are STIX/TAXII?
STIX and TAXII are the industry standards for sharing threat intelligence.
STIX/TAXII: Threat Intelligence Sharing Standards
STIX and TAXII are standards developed in an effort to improve the prevention and mitigation of cyber-attacks. STIX states the “what” of threat intelligence, while TAXII defines “how” that information is relayed. Unlike previous methods of sharing, STIX and TAXII are machine-readable and therefore easily automated.
STIX/TAXII aims to improve security measures in a few ways:
- Extend the capabilities of current threat intelligence sharing
- Balance response with proactive detection
- Encourage a holistic approach to threat intelligence
What is STIX?
STIX, short for Structured Threat Information eXpression, is a standardized language developed by MITRE and the OASIS Cyber Threat Intelligence (CTI) Technical Committee for describing cyber threat information. It has been adopted as an international standard by various intelligence sharing communities and organizations. It is designed to be shared via TAXII but can be shared by other means. STIX is structured so that users can describe threat:
- Motivations
- Abilities
- Capabilities
- Response
What is TAXII?
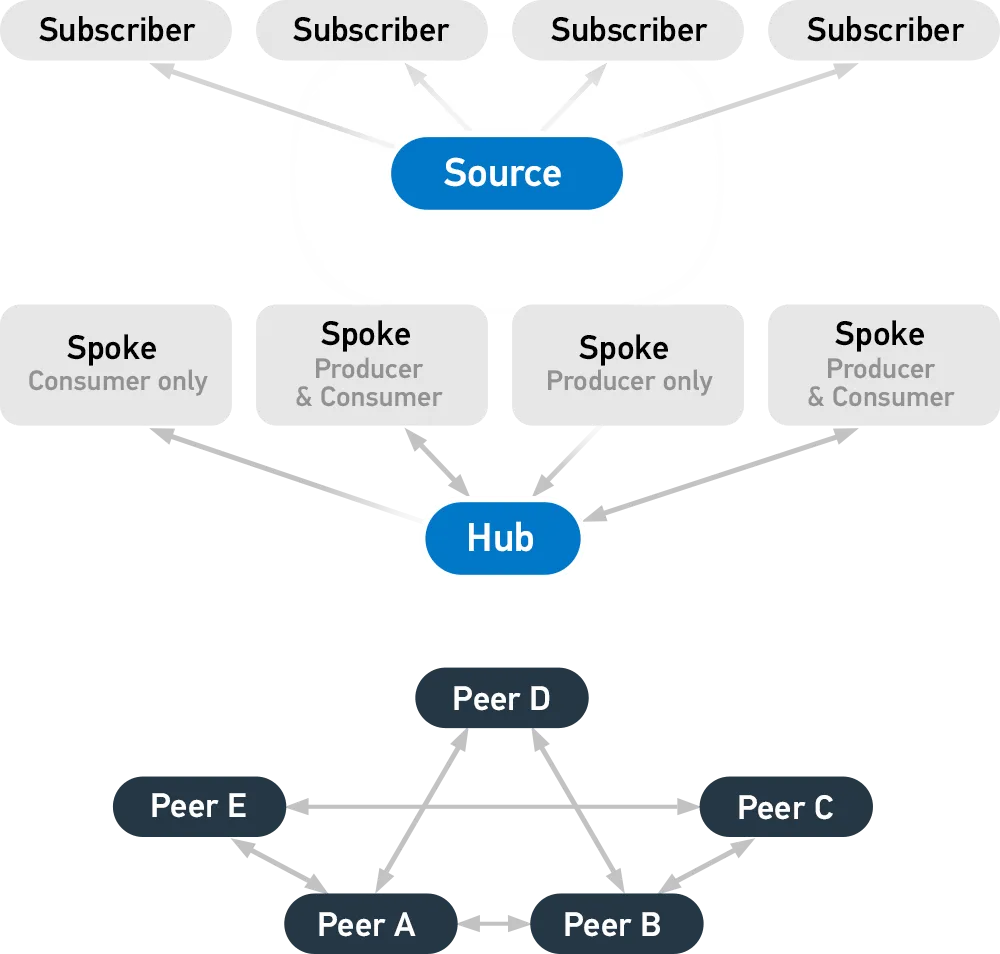
TAXII, short for Trusted Automated eXchange of Intelligence Information, defines how cyber threat information can be shared via services and message exchanges. It is designed specifically to support STIX information, which it does by defining an API that aligns with common sharing models. The three principal models for TAXII include:
- Hub and spoke – one repository of information
- Source/subscriber – one single source of information
- Peer-to-peer – multiple groups share information
TAXII defines four services. Users can select and implement as many as they require, and combine them for different sharing models.
- Discovery – a way to learn what services an entity supports and how to interact with them
- Collection Management – a way to learn about and request subscriptions to data collections
- Inbox – a way to receive content (push messaging)
- Poll – a way to request content (pull messaging)
STIX/TAXII Use Cases
STIX/TAXII supports a variety of use cases regarding cyber threat management. STIX/TAXII has been widely adopted by governments and Information Sharing and Analysis Centers (ISACs), which range in focus from industry to geolocation.
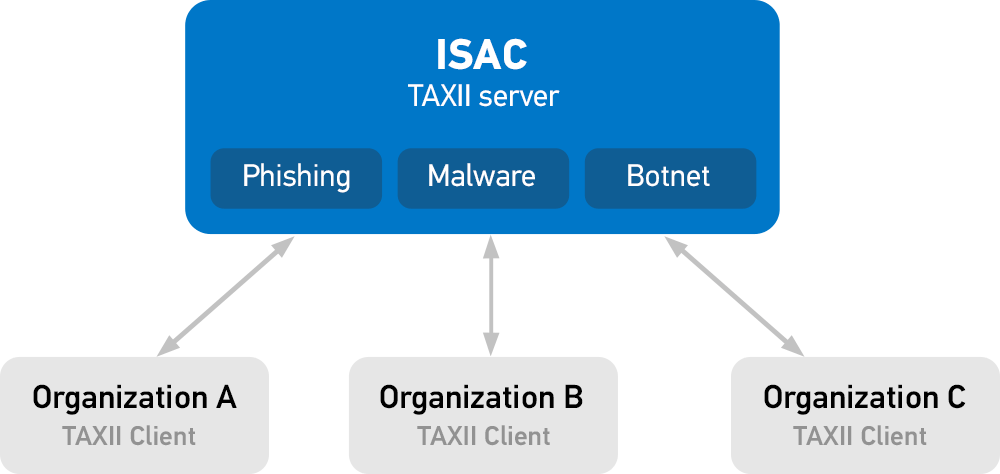
Sharing categorized information
Organizations can push and pull information into categories. For example, if one industry experiences a targeted phishing attack, they can share that information within the phishing category of the ISAC. Other organizations can automatically ingest that intelligence and bolster their own defenses.
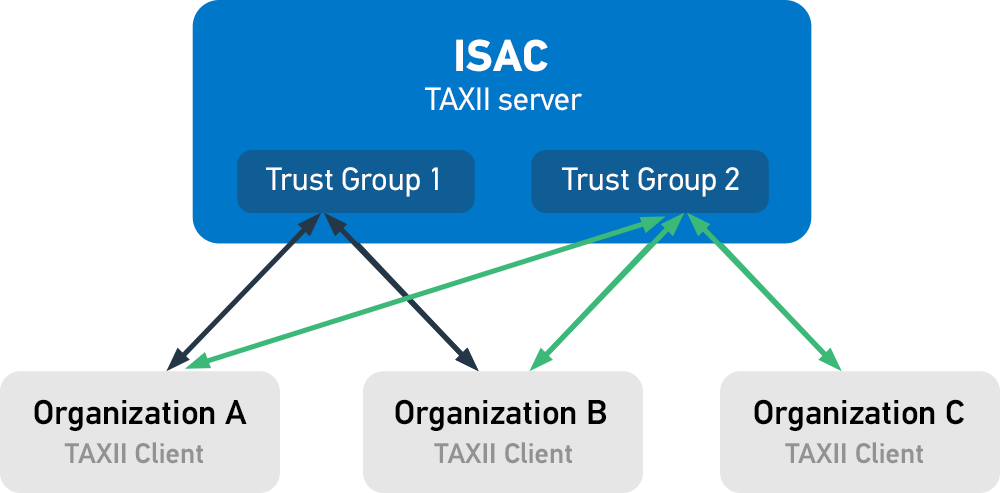
Sharing with groups
Organizations with a TAXII client can push and pull information into the TAXII servers of trusted sharing groups. Some organizations may have access to private groups within these ISACs that provide more detailed information.
STIX/TAXII Tools
Anomali provides a utility called STAXX that allows you to easily subscribe to any STIX/TAXII feed and push out indicators via STIX/TAXII for free. Get started in three simple steps:
Configure your data sources
Set up your download schedule
Signing up for an account on the STAXX portal allows users to link from an Indicator of Compromise (IOC) to information that identifies Threat Actors, Campaigns, and TTPs. Users can also access additional Anomali threat intelligence feeds as well as preview features of Anomali’s Threat Intelligence Platform, ThreatStream.
Online STIX/TAXII Resources
There are many ways to get involved with STIX/TAXII. If you’d like to engage with the community and contribute to creation efforts, you can join a committee within the OASIS TC. If you would like to learn more about STIX/TAXII, here are some additional resources:
STIX/TAXII overviews
STIX
- Detailed description of STIX 2.0 (Google Doc)
- Information on the differences between STIX 1.x/CybOX 2.x and STIX 2.0 (GitHub)