The Primary Sources of Cyberthreat Intelligence


Cyberthreat intelligence (CTI) is essential to modern cybersecurity strategies. It helps organizations anticipate, identify, and mitigate cyberthreats by gathering and analyzing information about potential adversaries. However, CTI’s effectiveness depends on the quality, relevance, and timeliness of the sources used. This blog explores the various sources of cyberthreat intelligence and how they contribute to a robust security posture.
Where Does CTI Come From?
CTI can be sourced from a wide range of locations, broadly categorized into four types: open source intelligence (OSINT), commercial intelligence sources, internal intelligence, and community intelligence.
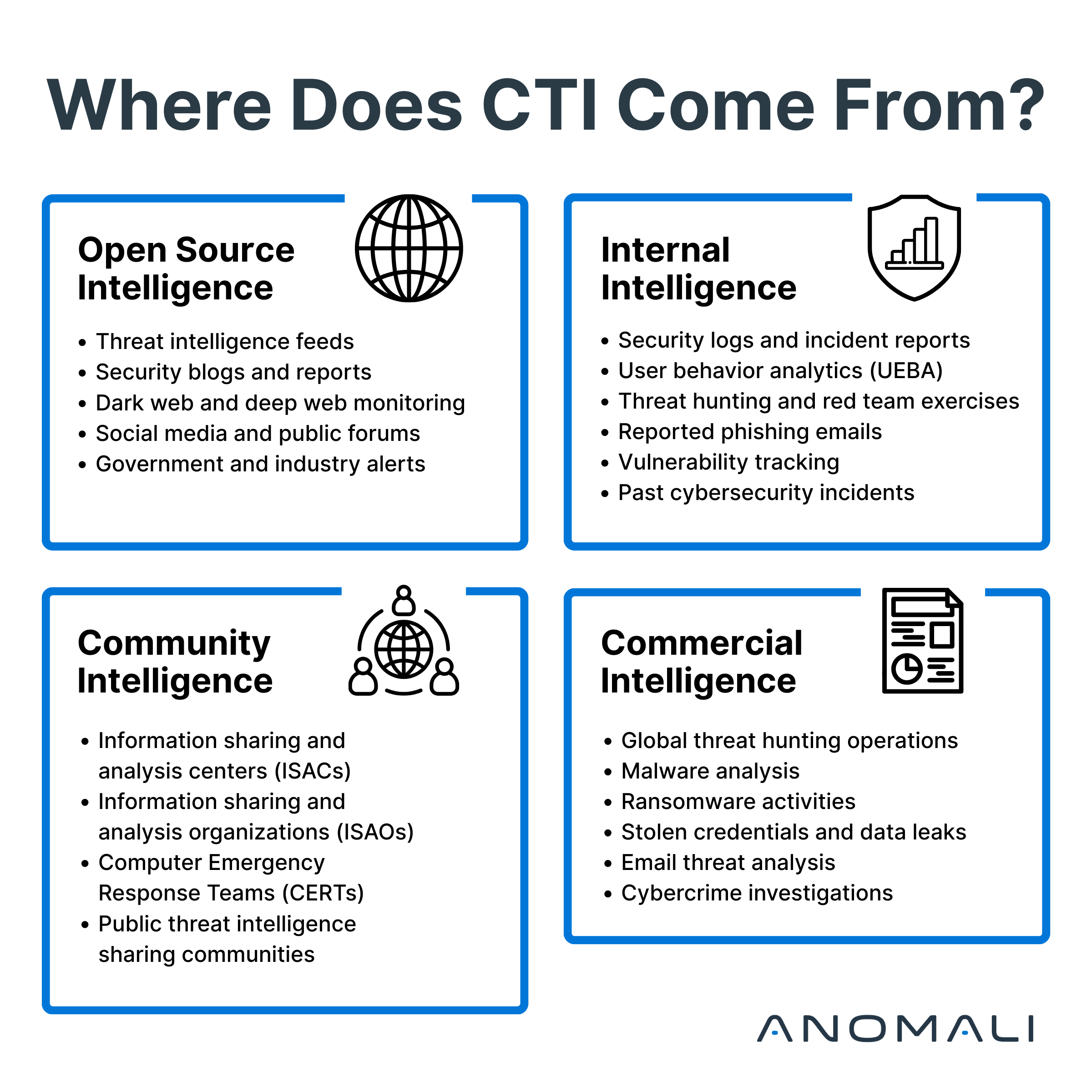
1. OSINT
Open source intelligence, or OSINT, is comprised of publicly available information that can be collected, analyzed, and used for threat detection. It includes:
- Threat intelligence feeds: These free feeds provide information on indicators of compromise (IoCs), malware signatures, and attack patterns.
- Security blogs and reports: Many cybersecurity firms and independent researchers publish reports detailing emerging threats.
- Dark web and deep web monitoring: Some OSINT projects monitor illicit forums, marketplaces, and communication channels that can provide insights into potential attacks, even before they strike.
- Social media and public forums: Hackers often communicate through social media and forums, making them valuable intelligence sources.
- Government and industry alerts: Organizations like CISA and NIST issue regular advisories on new threats, as do some computer emergency response teams (CERTs).
2. Commercial Threat Intelligence
Commercial cyberthreat intelligence is derived from various data sources that provide high-quality, real-time, and contextualized insights into cyberthreats.
- Global threat hunting operations: Commercial vendors deploy human-led investigations and AI-driven analytics to identify advanced threats.
- Malware analysis: Commercial vendors use automated malware analysis tools and sandbox environments to study malicious software behavior.
- Ransomware activities: Commercial vendors monitor discussions about ransomware as a service (RaaS) operators.
- Stolen credentials and data leaks: Commercial vendors track usernames, passwords, and sensitive data sold by cybercriminals.
- Email threat analysis: Commercial vendors identify malicious email attachments and phishing URLs.
- Cybercrime investigations: Commercial vendors track threat actors through intelligence operations.
3. Internal Threat Intelligence
Organizations generate their own intelligence by monitoring their networks, from analyzing past incidents, and from other security tools. Internal intelligence may include:
- Security logs and incident reports: Collecting logs from firewalls, intrusion detection systems (IDS), DNS, web proxy, and endpoint security solutions provides valuable insights into threats.
- User behavior analytics (UEBA): Tracking unusual behavior in user activity can help detect insider threats and compromised accounts.
- Threat hunting and red team exercises: Proactive security measures help organizations anticipate attacks before they materialize.
- Reported phishing emails: Suspicious emails reported by employees can help improve phishing attack detection.
- Vulnerability tracking: Identifies known security weaknesses in systems and applications.
- Past cybersecurity incidents: Reviewing attack vectors, malware strains, and attacker behaviors helps refine defenses and mitigate potential threats.
4. Community Threat Intelligence
Community-based threat intelligence data is gathered through collaborative efforts among cybersecurity professionals, researchers, and organizations. These communities share threat intelligence, indicators of compromise (IoCs), attack methodologies, and defensive strategies to strengthen global cybersecurity defenses. Below are the key sources of community-driven cyberthreat intelligence:
- Information sharing and analysis centers (ISACs): ISACs provide industry-specific threat data, best practices, and collaboration channels.
- Information sharing and analysis organizations (ISAOs): ISAOs are flexible, industry-agnostic groups that enable threat intel sharing among various entities.
- CERTs: CERTs are government-backed and industry-supported organizations that provide cyberthreat intelligence, alerts, and incident response guidance.
- Public threat intelligence sharing communities: Security researchers, ethical hackers, and organizations actively collaborate and share intelligence in these communities.
Best Practices for Sourcing Cyberthreat Intelligence
To ensure high-quality and actionable intelligence, organizations should:
- Validate and cross-check information: Not all intelligence sources are reliable. Always verify data from multiple sources before acting on it.
- Automate collection and analysis: Utilize machine learning and automation tools to efficiently process large volumes of data.
- Contextualize and prioritize threats: Intelligence should be relevant to your organization’s industry, infrastructure, and risk profile.
- Share intelligence responsibly: Participate in threat-sharing communities like ISACs to collaborate with industry peers.
- Update and refine sources regularly: Threat landscapes evolve quickly — so keep your intelligence sources updated to stay ahead.
Aggregating Intelligence Sources in Anomali ThreatStream
Anomali ThreatStream is the leading threat intelligence platform (TIP) designed to aggregate, analyze, and operationalize cyberthreat intelligence from various sources. It provides organizations with a vast library of cyberthreat intelligence feeds to enhance their overall security posture and proactively defend against emerging threats. Here’s an in-depth look at its key features and how it supports cybersecurity efforts:
- Deduplication: ThreatStream identifies and deduplicates redundant threat intelligence to eliminate noise and reduce alert fatigue.
- Data correlation: Correlates IoCs with live attack data to assess potential risks.
- Enrichment and contextualization: Enriches data with contextual insights, such as attacker profiles, tactics, techniques, and procedures (TTPs).
- Scoring and prioritization: Assigns confidence and severity scores to help security analysts prioritize legitimate threats and prevent false positives.
Anomali ThreatStream consolidates a variety of threat intelligence sources, including:
- OSINT: Publicly available data on cyberthreats, including malware analysis reports, security blogs, and government advisories.
- Commercial threat feeds: Integrates intelligence from premium security vendors for a more in-depth threat context.
- Private and internal intelligence: Allows organizations to incorporate their own threat intelligence, such as SIEM logs, network traffic, and incident reports.
- Industry-specific feeds: This initiative supports sector-specific threat feeds for the finance, healthcare, and government industries.
- ISAC/ISAO collaborations: This initiative enables information sharing through ISACs and ISAOs.
Leveraging Diverse, Credible, and Relevant Threat Intelligence Sources
Gathering a wide range of reliable cyberthreat intelligence sources is crucial in building a proactive cybersecurity defense. By leveraging OSINT, commercial intelligence, internal insights, and community intelligence, organizations can gain a well-rounded understanding of cyberthreats and take appropriate action. A structured approach to CTI sourcing and best practices ensures resilience against the ever-evolving cyberthreat landscape.
If you’d like to see how world-class threat intelligence can transform your organization’s security posture, request a demo of Anomali Security and IT Operations Platform.
Stay vigilant, stay informed, and keep your cybersecurity defenses strong!
FEATURED RESOURCES

Anomali Cyber Watch: Notepad++ Attack, RAT Uses Hugging Face, Microsoft Office Flaw and more



