Harness the Power of Global Threat Intelligence
Operationalize data and insights to secure your organization. Anomali ThreatStream provides access to the industry's largest global repository of curated threat intelligence — delivering enrichment, contextualization, and detection of known and emerging threats — tailored specifically to your organization.


Immediately Transform Raw Data Into Actionable Intelligence
Stop attacks before they start. Anomali ThreatStream correlates enriched threat intelligence with relevant telemetry to drive informed decisions and act with confidence.
Relevant Intelligence
Connect to the global community of cybersecurity researchers with curated access to hundreds of diverse feeds in the world's largest repository of curated, actionable threat intelligence.
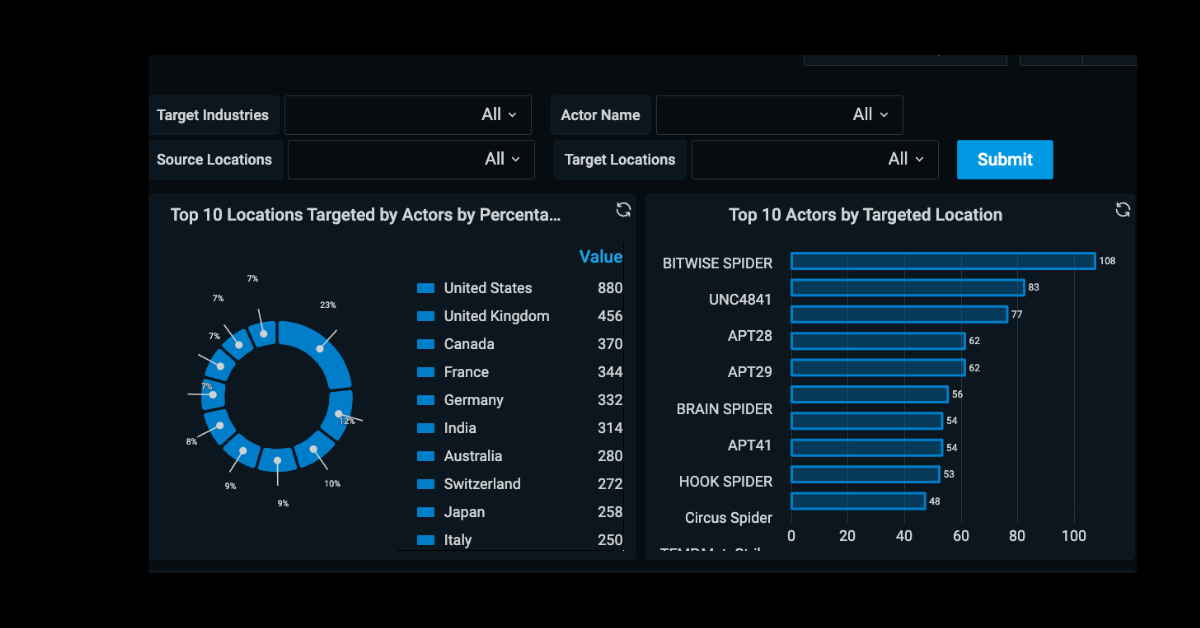
Personalized Insights
Out-of-the-box dashboards tailored to your organization provide threat intelligence teams with critical threat status in real time. ThreatStream automatically correlates threat intelligence with vulnerabilities in your environment, empowering rapid investigation and effective response.
Automated Distribution
Seamlessly share enriched threat intelligence across your entire security ecosystem to enable proactive blocking and monitoring of potential attacks, strengthen your security posture, and reduce risk.
Product Features
What People Are Saying About Anomali
Turbocharge Your Threat Intelligence
Integrations with leading vendors are included with every ThreatStream and Integrator subscription, enabling your security team to accelerate investigation and response times, optimize your security stack, and automate SOC operations.
Recognized as a Leader in Modernizing Security Operations








Be Different.
Be the Anomali.
Challenge the status quo with a different type of threat intelligence platform.